This CloudFormation Snippets extension equips Visual Studio Code with JSON and YAML snippets for all AWS CloudFormation and SAM resources - over 1250+ in total. It's your complete toolset for efficient CloudFormation template development.
Tip
Stop AWS bill surprises from happening.
Most infrastructure changes look harmless until you see next month's AWS bill. CloudBurn prevents this by analyzing the cost impact of your AWS CDK changes directly in GitHub pull requests, catching expensive mistakes during code review when fixes are quick, not weeks later when they're costly and risky.
💰 Set it up once, then never be surprised by AWS costs again
- First install the free CDK Diff PR Commenter GitHub Action in your repository where you build your AWS CDK infrastructure
- Then install the CloudBurn GitHub App on the same repository
What happens now:
Whenever you open a PR with infrastructure changes, the GitHub Action comments with your CDK diff analysis. CloudBurn reads that diff and automatically adds a separate comment with a detailed cost report showing:
- Monthly cost impact – Will this change increase or decrease your AWS bill? By how much?
- Per-resource breakdown – See exactly which resources are driving costs (old vs. new monthly costs)
- Region-aware pricing – We pick the right AWS pricing based on the region where your infrastructure is deployed
Your team can now validate cost impact alongside infrastructure changes during code review. Essentially, this shifts FinOps left where you optimize costs as you code, not weeks later when context is lost and production adjustments require more time and carry added risk.
CloudBurn will be free during beta. After launch, a free Community plan (1 repository with unlimited users) will always be available.
- Comprehensive Coverage: Offers snippets for all AWS CloudFormation and AWS SAM resources available - that's over 1250+ resources snippets at your fingertips!
- Complete Property Support: Includes all nested properties for each resource, ensuring you have access to every configurable aspect of your AWS resources.
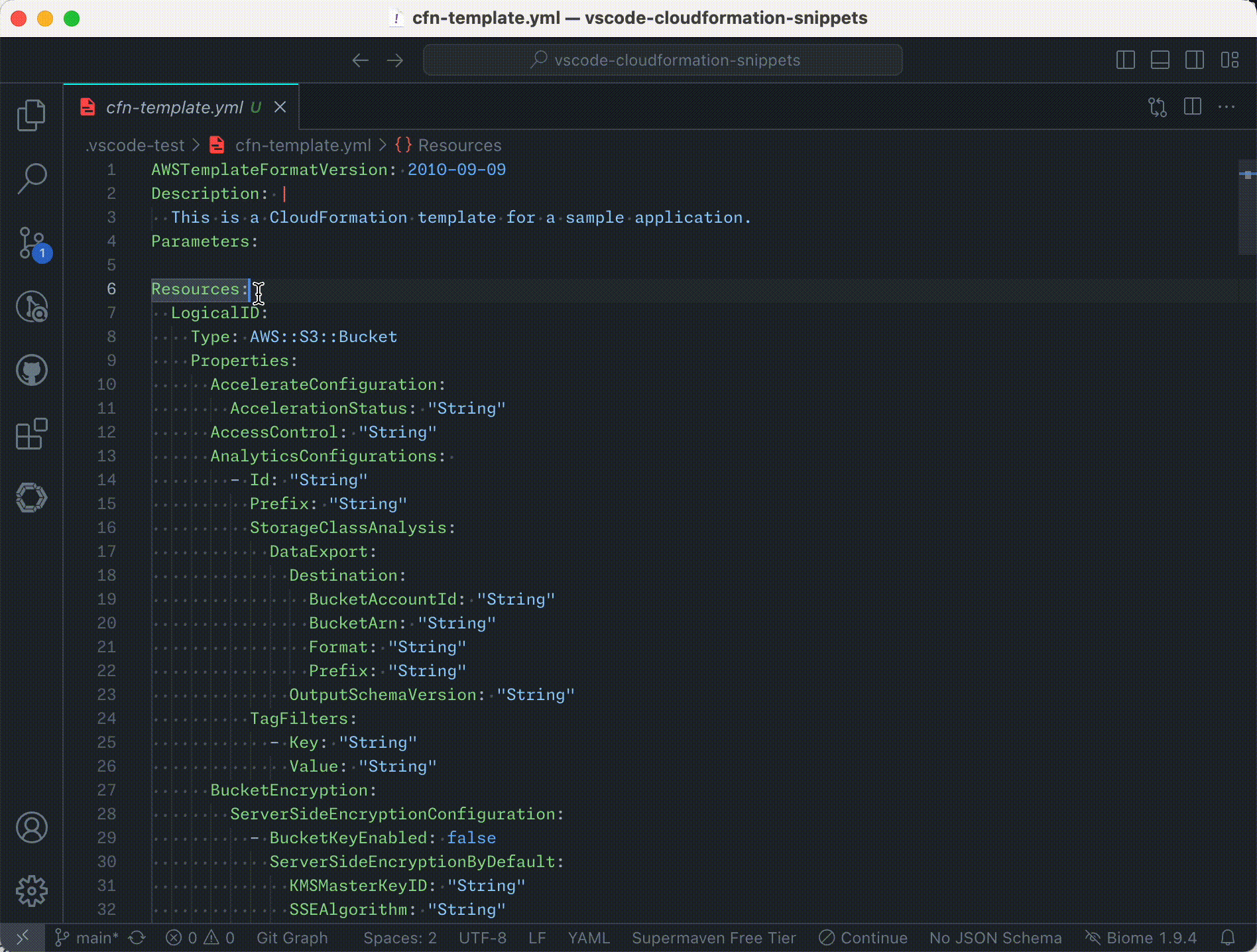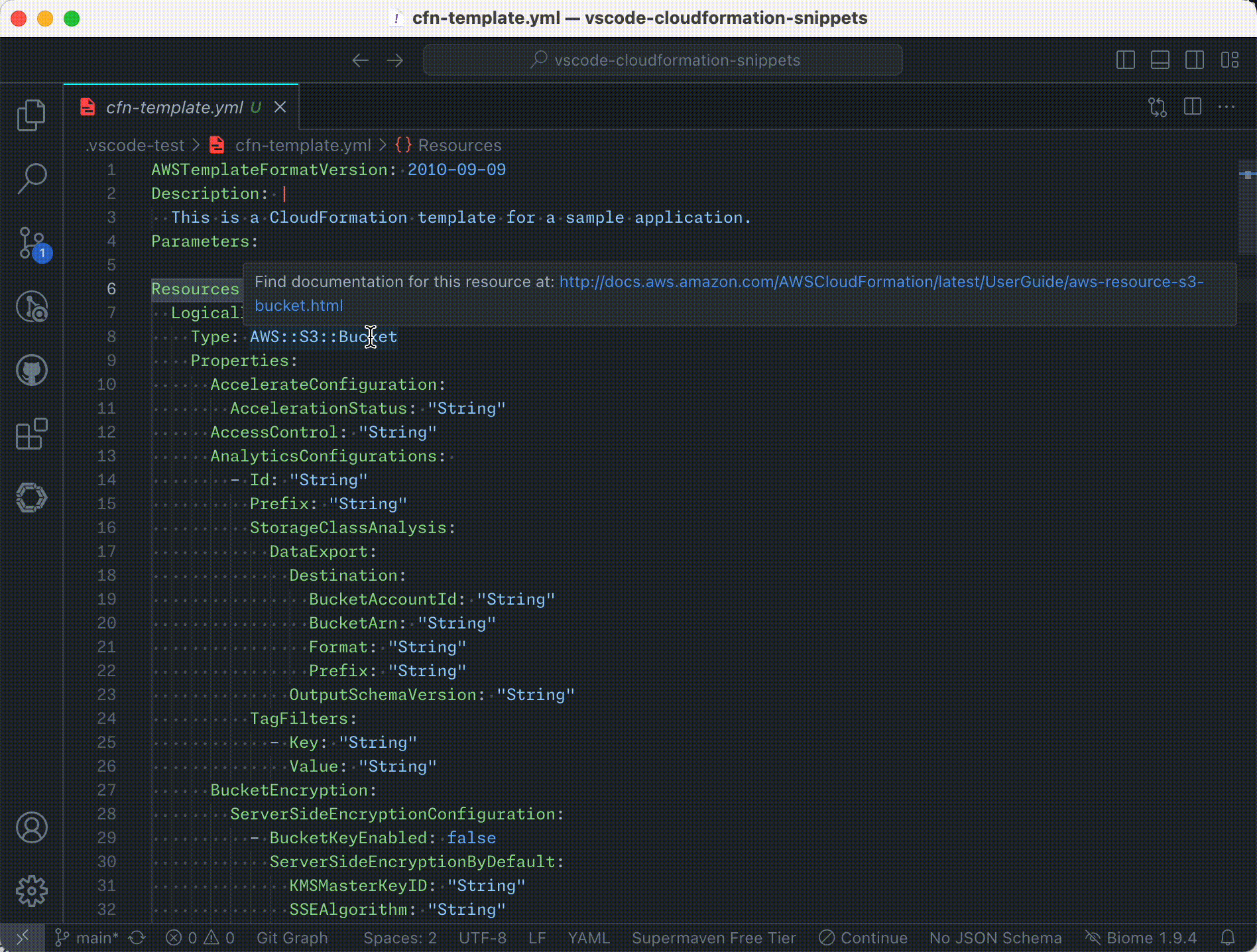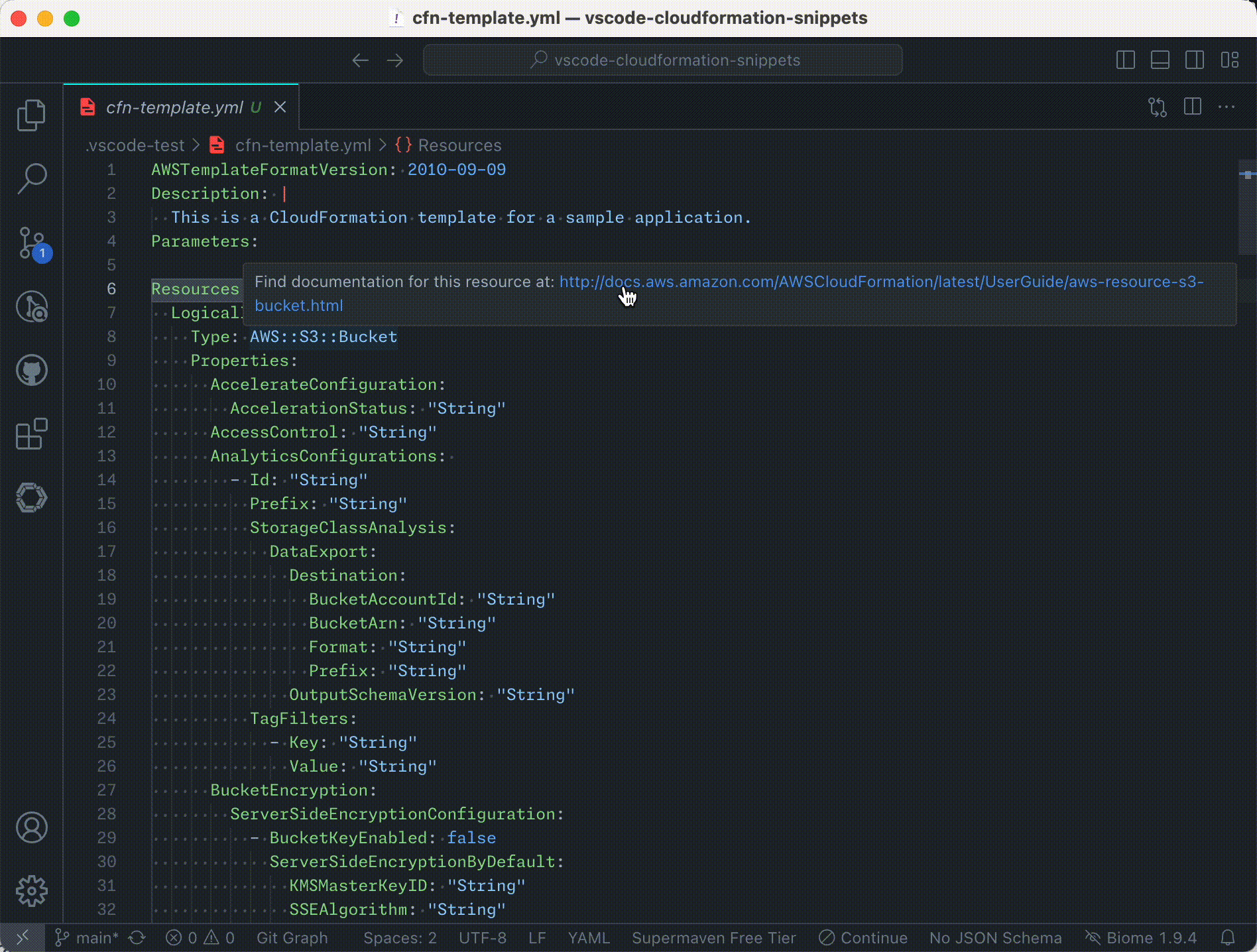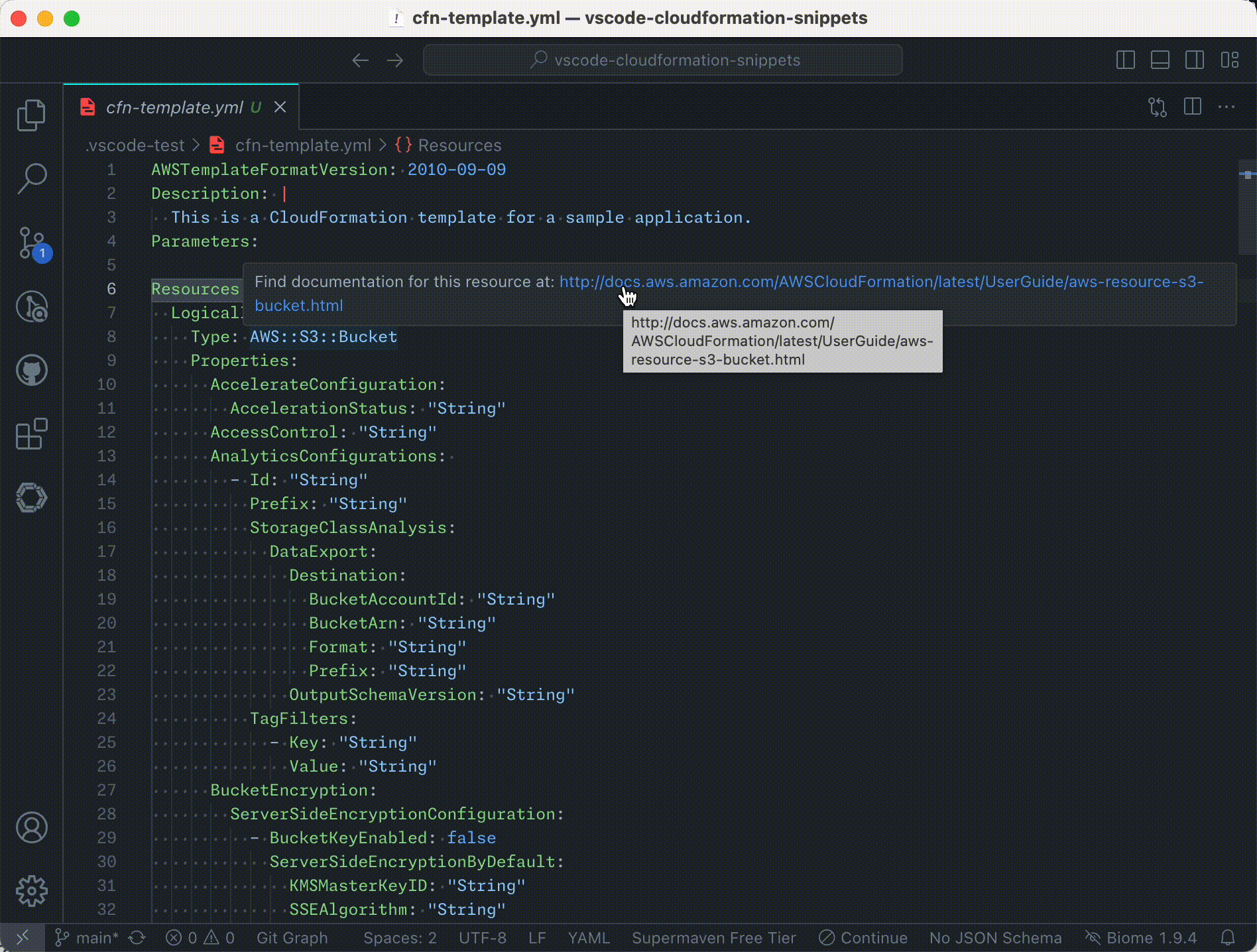
- Documentation Hover Links: Quickly access AWS CloudFormation resource and property documentation by hovering over resource types and property names in your templates.
- Flexible Template Support: Seamlessly works with both YAML and JSON CloudFormation templates.
- Efficient Autocomplete: Simply type the resource name (e.g.,
ec2-instance) to instantly load the corresponding snippet forAWS::EC2::Instance. - Rich Feature Set: Incorporates intrinsic functions, conditions, and diverse parameter types for robust template creation.
- Enhanced Navigation: Features placeholders that enable swift movement through resource properties.
- Resource Documentation: Each snippet is linked to its official AWS documentation, providing quick access to detailed information.
- Up-to-Date: Regularly refreshed on a weekly basis to reflect the latest CloudFormation Resource Specification.
- Gitpod Ready: Made available on the Open VSX Registry to ensure compatibility with Gitpod.
- Install the CloudFormation Snippets extension in VS Code.
- Create a new
.ymlor.jsonfile. - Ensure the file type is set to "YAML" or "JSON" in the bottom right corner of VS Code.
- Type cfn to insert the basic CloudFormation template structure.
- Add resources using their short prefix (e.g.
s3-bucketforAWS::S3::Bucket).
Example of auto-completion in action:
and an example of the hover information:
Note: Once you start typing a prefix (explained in step 5), the corresponding snippet will show up in the dropdown menu. If this doesn't happen automatically, press
ctrl + spaceto invoke IntelliSense and search for the prefix of the resource type that you want to add (as listed in step 5).
We've developed the AWS CloudFormation Starterkit to streamline your infrastructure setup using CloudFormation.
It comes with pre-configured templates, automated validation scripts, and seamless integration with CI/CD pipelines, you'll be able to deploy robust, scalable, and secure AWS environments with ease.
The starterkit empowers you to adopt best practices effortlessly. By leveraging tools like Checkov for security compliance and cfn-lint for template validation, you ensure that your infrastructure is both reliable and secure.
If you have a feature request or an issue, please let me know on Github