... Powered by 📦
... Running on k3s, Truenas
... Managed by ArgoCD (GitOps), Renovate
... And a little bit of ☁️ AWS, and GitHub Actions_ 🤖
Today is automated via Jailmaker. Bootstrap script can be found in truenas/k3s-jail-config.
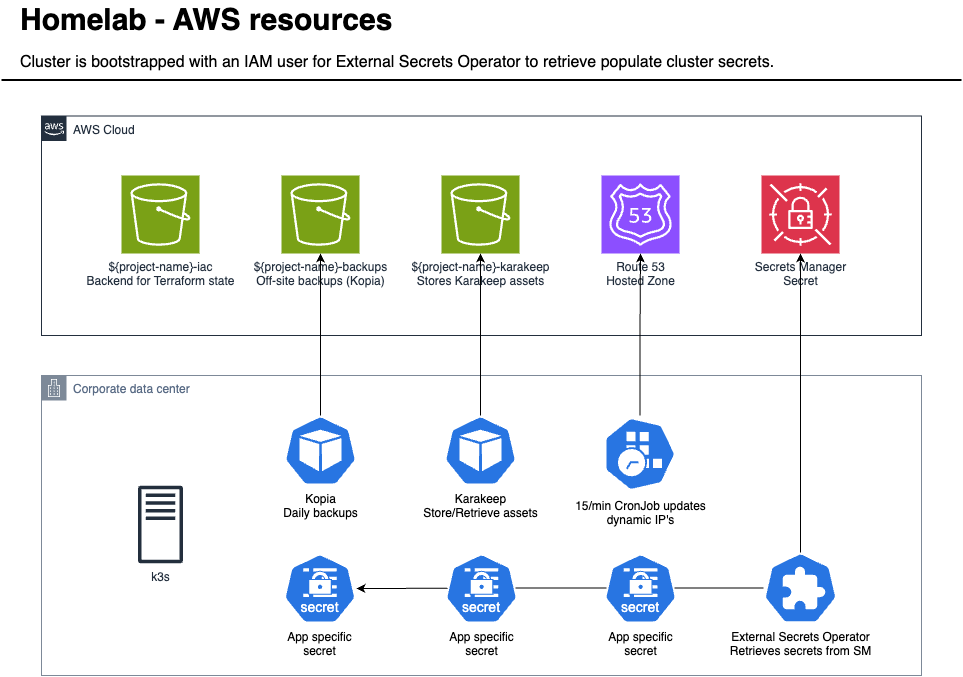
Create an IAM user with the following policy attached:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "Get",
"Effect": "Allow",
"Action": "secretsmanager:GetSecretValue",
"Resource": "arn:aws:secretsmanager:*:<AWS account id>:secret:k8s*"
},
{
"Sid": "List",
"Effect": "Allow",
"Action": "secretsmanager:ListSecrets",
"Resource": "*"
}
]
}This gives access to secrets prefixed with k8s. Your secrets can now be stored
in AWS Secrets Manager.
# To bootstrap, we add AWS credentials via one secret:
printf "%s" "Enter ACCESS_KEY: "
read ACCESS_KEY
printf "%s" "Enter SECRET_KEY: "
read SECRET_KEY
kubectl create ns external-secrets
kubectl create secret generic awssm-secret -n external-secrets \
--from-literal=access-key=$ACCESS_KEY --from-literal=secret-access-key=$SECRET_KEYMultiple services like Cert-Manager and DDNS rely on external secrets that are bootstrapped via the above.




)


